Библиотека сайта rus-linux.net
The book is available and called simply "Understanding The Linux Virtual Memory Manager". There is a lot of additional material in the book that is not available here, including details on later 2.4 kernels, introductions to 2.6, a whole new chapter on the shared memory filesystem, coverage of TLB management, a lot more code commentary, countless other additions and clarifications and a CD with lots of cool stuff on it. This material (although now dated and lacking in comparison to the book) will remain available although I obviously encourge you to buy the book from your favourite book store :-) . As the book is under the Bruce Perens Open Book Series, it will be available 90 days after appearing on the book shelves which means it is not available right now. When it is available, it will be downloadable from http://www.phptr.com/perens so check there for more information.
To be fully clear, this webpage is not the actual book.
Next: 6. Boot Memory Allocator Up: 5. Process Address Space Previous: 5.6 Page Faulting Contents Index
5.7 Copying To/From Userspace
It is not safe to access memory in the process address space directly as
there is no way to quickly check if the page addressed is resident or not.
Linux relies on the MMU to raise exceptions when the address is invalid
and have the Page Fault Exception handler catch the exception and fix it
up. In the x86 case, assembler is provided by the __copy_user()
to trap exceptions where the address is totally useless. The location of the
fixup code is found when the function search_exception_table()
is called. Linux provides an ample API (mainly macros) for copying data to
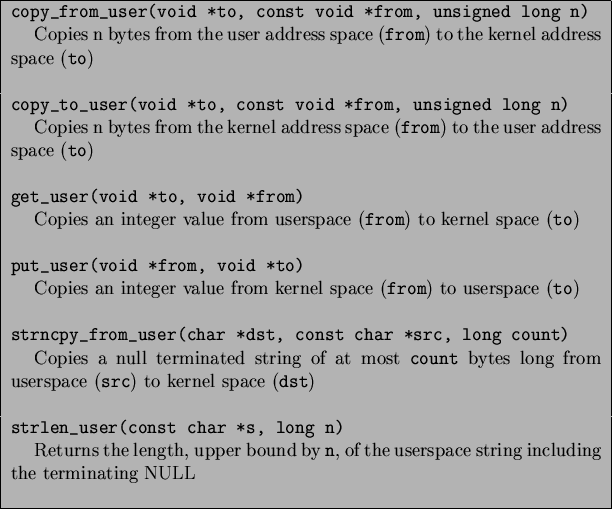
and from the user address space safely as shown in Table 5.5.
All the macros map on to assembler functions which all follow similar
patterns of implementation so for illustration purposes, we'll just trace
how copy_from_user() is implemented on the x86.
copy_from_user() calls either
__constant_copy_from_user() or
__generic_copy_from_user() depending on whether the size of
the copy is known at compile time or not. If the size is known at compile
time, there are different assembler optimisations to copy data in 1, 2 or
4 byte strides otherwise the distinction between the two copy functions is
not important.
The generic copy function eventually calls the function
__copy_user_zeroing() in ![]()
asm-i386/uaccess.h![]() which has three important parts. The first part is the assembler for the
actual copying of
which has three important parts. The first part is the assembler for the
actual copying of size number of bytes from userspace. If any
page is not resident, a page fault will occur and if the address is valid,
it will get swapped in as normal. The second part is ``fixup'' code and the
third part is the __ex_table mapping the instructions from the
first part to the fixup code in the second part.
These pairings of execution points and fixup routines, as described
in Section 5.5, are copied to the kernel
exception handle table by the linker. If an invalid address is
read, the function do_page_fault() will fall through, call
search_exception_table() and find the EIP where the faulty read
took place and jump to the fixup code which copies zeros into the remaining
kernel space, fixes up registers and returns. In this manner, the kernel
can safely access userspace with no expensive checks and letting the MMU
hardware handle the exceptions.
All the other functions that access userspace follow a similar pattern.
Next: 6. Boot Memory Allocator Up: 5. Process Address Space Previous: 5.6 Page Faulting Contents Index Mel 2004-02-15







![\includegraphics[width=17cm]{graphs/do_page_fault_flow.ps}](/MyLDP/BOOKS/VirtMem/img41.png)