Библиотека сайта rus-linux.net

Chapter 4. Windows NT Domains
In addition to the domain features of that we discussed in Chapter 1, having a domain makes it possible to use logon scripts and roaming profiles (also called roving profiles). A logon script is a text file of commands that are run during startup, and a profile is a collection of information regarding the desktop environment, including the contents of the Start menu, icons that appear on the desktop, and other characteristics about the GUI environment that users are allowed to customize. A roaming profile can follow its owner from computer to computer, allowing her to have the same familiar interface appear wherever she logs on.
A Windows NT domain offers centralized control over the network. Policies can be set up by an administrator to define aspects of the users' environment and limit the amount of control they have over the network and their computers. It is also possible for administrators to perform remote administration of the domain controllers from any Windows NT/2000/XP workstation.
Samba 2.2 has the ability to act as a primary domain controller, supporting domain logons from Windows 95/98/Me/NT/2000/XP computers and allowing Windows NT/2000/XP[1] systems to join the domain as domain member servers. Samba can also join a domain as a member server, allowing the primary domain controller to be a Windows NT/2000 system or another Samba server.
TIP
Samba 2.2 does not support LDAP and Kerberos authentication of Active Directory, so it cannot act as a Windows 2000 Active Directory domain controller. However, Samba can be added to an Active Directory domain as a member server, with the Windows 2000 domain controllers running in either mixed or native mode. The Windows 2000 server (even if it is running in native mode) supports the Samba server by acting as a PDC emulator, using the Windows NT style of authentication rather than the Kerberos style.
-
Configuring and using Samba as the primary domain controller
-
Configuring logon scripts, roaming profiles, and system policies
Samba as the Primary Domain Controller
TIP
TIP
If you would like more information on how to set up domains, see the file Samba-PDC-HOWTO.html in the docs/htmldocs directory of the Samba source distribution.
TIP
Although Samba 2.2 cannot function as, or work with, a Windows NT BDC, it is possible to set up another Samba server to act as a backup for a Samba PDC. For further information, see the file Samba-BDC-HOWTO.html in the docs/htmldocs directory of the Samba source distribution.
Modifying smb.conf
First you will need to start with an
smb.conf file that correctly configures Samba for
workgroup computing, such as the one we created in Chapter 2, and insert the following lines into the
[global] section:
[global]
; use the name of your Samba server instead of toltec
; and your own workgroup instead of METRAN
netbios name = toltec
workgroup = METRAN
encrypt passwords = yes
domain master = yes
local master = yes
preferred master = yes
os level = 65
security = user
domain logons = yes
; logon path tells Samba where to put Windows NT/2000/XP roaming profiles
logon path = \\%L\profiles\%u\%m
logon script = logon.bat
logon drive = H:
; logon home is used to specify home directory and
; Windows 95/98/Me roaming profile location
logon home = \\%L\%u\.win_profile\%m
time server = yes
; instead of jay, use the names of all users in the Windows NT/2000/XP
; Administrators group who log on to the domain
domain admin group = root jay
; the below works on Red Hat Linux - other OSs might need a different command
add user script = /usr/sbin/useradd -d /dev/null -g 100 -s /bin/false -M %uAnd after the [global] section, add these three
new shares:
[netlogon]
path = /usr/local/samba/lib/netlogon
writable = no
browsable = no
[profiles]
; you might wish to use a different directory for your
; Windows NT/2000/XP roaming profiles
path = /home/samba-ntprof
browsable = no
writable = yes
create mask = 0600
directory mask = 0700
[homes]
read only = no
browsable = no
guest ok = no
map archive = yesNow for the explanation. If you are comparing this example to the
configuration file presented in Chapter 2, you
will notice that the first three parameter settings are similar. We
start out in the [global] section by setting the
NetBIOS name of the Samba server. We are using the default, which is
the DNS hostname, but are being explicit because the NetBIOS name is
used in UNCs that appear later in smb.conf. The
next two lines, setting the workgroup name and choosing to use
encrypted passwords, are identical to our
smb.conf file from Chapter 2.
However, things are now a little different: even though it still
reads "workgroup", we are actually
setting the name of the domain. For a workgroup, using encrypted
passwords is optional; when using a domain, they are required.
The next four lines set up our Samba PDC to handle browsing services.
The line domain master
= yes causes Samba to be the
domain master browser, which handles browsing services for the domain
across multiple subnets if necessary. Although it looks very similar,
local master
= yes does not cause Samba to
be the master browser on the subnet, but merely tells it to
participate in browser elections and allow itself to win. (These two
lines are yet more default settings that we include to be clear.) The
next two lines ensure that Samba wins the elections. Setting the
preferred master parameter
makes Samba force an election when it starts up. The
os level parameter is set
higher than that of any other system, which results in Samba winning
that election. (At the time of this writing, an os
level of 65 was sufficient to win over all versions of
Windows—but make sure no other Samba server is set higher!) We
make sure Samba is both the domain and local master browser
because Windows NT/2000 PDCs always reserve the domain master browser
role for themselves and because Windows clients require things to be
that way to find the primary domain controller. It is possible to
allow another computer on the network to win the role of local master
browser, but having the same server act as both domain and local
masters is simpler and more efficient.
The next two lines in the [global] section set up
Samba to handle the actual domain logons. We set
security =
user so that Samba will require a username and
password. This is actually the same as in the workgroup setup we
covered in Chapter 1 and Chapter 2 because it is the default. The only
reason we're including it explicitly is to avoid
confusion: another valid setting is security
= domain, but that is for
having another (Windows or Samba) domain controller handle the logons
and should never be found in the smb.conf of a
Samba PDC. The next line, domain
logons =
yes, is what tells Samba we want this server to
handle domain logons.
Defining a logon path is necessary for supporting
roaming profiles for
Windows NT/2000/XP clients. The UNC
\\%L\profiles\%u refers to a share held on the
Samba server where the profiles are kept. The variables
%L and %u are replaced by Samba
with the name of the server and the username of the logged on user,
respectively. The section in smb.conf defining
the [profiles] share contains the definition of
exactly where the profiles are kept on the server.
We'll get back to this topic a bit later in this
chapter.
Setting time server
= yes causes Samba to advertise
itself as a time service for the network. This is
optional.
The last parameter to add to the [global] section
is add user
script, and you will need it only if one or more
of your clients is a Windows NT/2000/XP system. We will tell you more
about this in Section 4.2 later in this chapter.
The rest of the additions to smb.conf are the
definitions for three shares. The
[netlogon] share is necessary for Samba to
handle domain logons because Windows clients need to connect to it
during the logon process and will fail if the share does not exist.
Other than that, the only function of [netlogon]
is to be a repository for logon scripts and system-policy files,
which we shall cover in detail later in this chapter. The path to a
directory on the Samba server is given, and because the clients only
read logon scripts and system-policy files from the share, the
writable =
no definition is used to make the share read-only.
Users do not need to see the share, so we set
browsable =
no to make the share invisible.
The [profiles] share is needed for use with
Windows NT/2000/XP roaming profiles. The path points to a directory
on the Samba server where the profiles are kept, and in this case,
the clients must be able to read and write the profile data. The
create mask (read and write
permitted for the owner only) and directory
mask (read, write, and search permitted for the
owner only) are set up such that a user's profile
data can be read and written only by the user and not accessed or
modified by anyone else.
The [homes] share is necessary for our
definitions of logon drive and
logon home to work. Samba uses
the [homes] share to add the home directory of the
user (found in /etc/passwd ) as a share. Instead
of appearing as "homes", the share
will be accessible on the client through a folder having the same
name as the user's username. We will cover this
topic in more detail in Chapter 9.
At this point, you might want to run testparm to check your smb.conf file.
Creating Directories on the Samba Server
The
[netlogon] and [profiles]
shares defined in our new smb.conf file
reference directories on the Samba server, and it is necessary to
create those directories with the proper permissions:
#mkdir /usr/local/samba/lib/netlogon#chmod 775 /usr/local/samba/lib/netlogon#mkdir /home/samba-ntprof#chmod 777 /home/samba-ntprof
The directory names we use are just examples. You are free to choose your own.
Adding Computer Accounts
To interact in a domain, a Windows NT/2000/XP system must be a member of the domain. Domain membership is implemented using computer accounts, which are similar to user accounts and allow a domain controller to keep information with which to authenticate computers on the network. That is, the domain controller must be able to tell if requests that arrive from a computer are coming from a computer that it "knows" as being part of the domain. Each Windows NT/2000/XP system in the domain has a computer account in the domain controllers' database, which on a Windows NT/2000 hosted domain is the SAM database. Although Samba uses a different method (involving the smbpasswd file), it also treats computer accounts similarly to user accounts.
To create a computer account, an administrator configures a Windows NT/2000/XP system to be part of the domain. For Samba 2.2, the "domain administrator" is the root account on the Samba server, and you will need to run the command:
#smbpasswd -a root
With Samba 2.2, an entry is also required in the /etc/passwd file[2] to give the computer account a user ID (UID) on the Samba server.
This account will never be used to
log in to the Unix system, so it should not be given a valid home
directory or login shell. To make this part work, you must set the
add user
script parameter in your Samba configuration file,
using a command that adds the entry in the proper manner. On our Red
Hat Linux system, we set add
user script to:
/usr/sbin/useradd -d /dev/null -g 100 -s /bin/false -M %u
This command adds an entry in /etc/passwd similar to the following:
aztec$:x:505:100::/dev/null:/bin/false
Again, notice that the username ends in a dollar sign. The user
account shown has a "home
directory" of /dev/null, a
group ID (GID) of 100, and a "login
shell" of /bin/false. The
-M flag in our useradd
command prevents it from creating the home directory. Samba replaces
the %u variable in the
useradd command with the NetBIOS name of the
computer, including the trailing dollar sign. The basic idea here is
to create an entry with a valid username and UID. These are the only
parts that Samba uses. It is important that the UID be unique, not
also used for other accounts—especially ones that are
associated with Samba users.
If you are using some other variety of Unix, you will need to replace our useradd command with a command that performs the same function on your system. If a command such as useradd does not come with your system, you can write a shell script yourself that performs the same function. In any case, the command should add a password hash that does not correspond to any valid password. For example, in the /etc/shadow file of our Linux server, we find the following two lines:
jay:%1%zQ7j7ok8$D/IubyRAY5ovM3bTrpUCn1:11566:0:99999:7::: zapotec$:!!:11625:0:99999:7:::
The first line is for jay's user
account. The second field is the password hash—the long string
between the first and second colons. The second line is for the
computer account of zapotec, a domain member
server. Its "username" ends with a
dollar sign ($), and the second field in this case
has been set to "!!", which is an
arbitrary string not produced from any password. Therefore, there is
no valid password for this account on the Linux host. Just about any
ASCII string can be used instead of
"!!". For example, you could use
"DISABLED" instead.
TIP
It is possible to create the entries for /etc/passwd and smbpasswd manually; however, we suggest this method be used very carefully, and only for initial testing, or as a last resort. The reason for this is to maintain security. After the computer account has been created on the server, the next Windows NT/2000/XP system on the network with a matching NetBIOS name to log on to the domain will be associated with this account. This allows crackers a window of opportunity to take over computer accounts for their own purposes.
Configuring Windows Clients for Domain Logons
Windows 95/98/Me
To
enable domain logons with Windows 95/98/Me, open the Control Panel
and double-click the Network icon. Then click Client for Microsoft
Networks, and click the Properties button. At this point, you should
see a dialog box similar to Figure 4-1. Select the
Logon to Windows Domain checkbox at the top of the dialog box, and
enter the name of the domain as you have defined it with the
workgroup parameter in the Samba configuration
file. Then click OK, and reboot the machine when asked.
Figure 4-1. Configuring a Windows 95/98 client for domain logons
WARNING
If Windows complains that you are already logged into the domain, you probably have an active connection to a share in the workgroup (such as a mapped network drive). Simply disconnect the resource temporarily by right-clicking its icon and choosing the Disconnect pop-up menu item.
User-Level Security for Windows 95/98/Me
Now that you have a primary domain controller to authenticate users, you can implement much better security for shares that reside on Windows 95/98/Me systems.[3] To enable this functionality, open the Control Panel, double-click the Network icon, and click the Access Control tab in the dialog box. The window should now look like Figure 4-2.
Figure 4-2. Setting user-level access control
Click the User-level access control radio button, and type in the name of your domain in the text area. Click the OK button. If you get the dialog box shown in Figure 4-3, it means that shares are already on the system.
Figure 4-3. Error dialog while changing to user-level access control
After rebooting, you can create shares with user-level access control. To do this, right-click the folder you wish to share, and select Sharing.... This will bring up the Shared Properties dialog box, shown in Figure 4-4.
Figure 4-4. The Shared Properties dialog
Click the Shared As: radio button, and give the share a name and comment. Then click the Add... button, and you will see the Add Users dialog box, shown in Figure 4-5.
Figure 4-5. The Add Users dialog
What has happened is that Windows has contacted the primary domain controller (in this case, Samba) and requested a list of domain users and groups. You can now select a user or group and add it to one or more of the three lists on the righthand side of the window—for Read Only, Full Access, or Custom Control—by clicking the buttons in the middle of the window. When you are done, click the OK button. If you added any users or groups to the Custom Control list, you will be presented with the Change Access Rights dialog box, shown in Figure 4-6, in which you can specify the rights you wish to allow. Then click the OK button to close the dialog box.
Figure 4-6. The Change Access Rights dialog
You are now returned to the Shared Properties dialog box, where you will see the Name: and Access Rights: columns filled in with the permissions that you just created. Click the OK button to finalize the process. Remember, you will have to perform these actions on any folders that you had previously shared using share-level security.
Windows NT 4.0
To configure Windows NT for domain logons, log in to the computer as Administrator or another user in the Administrators group, open the Control Panel, and double-click the Network icon. If it isn't already selected, click on the Network Identification tab.
Click the Change... button, and you should see the dialog box shown
in Figure 4-7. In this dialog box, you can choose
to have the Windows NT client become a member of the domain by
clicking the checkbox marked Domain: in the Member of box. Then type
in the name of the domain to which you wish the client to log on; it
should be the same as the one you specified using the
workgroup parameter in the Samba configuration
file. Click the checkbox marked Create a Computer Account in the
Domain, and fill in "root" for the
text area labeled User Name:. In the Password: text area, fill in the
root password you gave smbpasswd for creating
computer accounts.
Figure 4-7. Configuring a Windows NT client for domain logons
WARNING
WARNING
After you enter the password, Windows NT should consult the primary domain controller (Samba) to see if the password is correct. Again, you can check the log files if you want to see this in action. If it worked, you have successfully configured Samba to act as a domain controller for Windows NT machines.
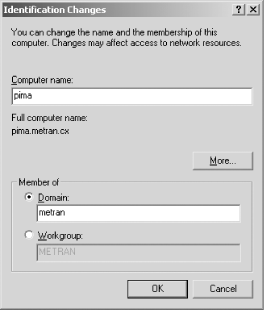
Windows 2000
To configure Windows 2000 for domain logons, log in to the computer as Administrator or another user in the Administrators group, open the Control Panel, and double-click the System icon to open the System Properties dialog box. Click the Network Identification tab, and then click the Properties button. You should now see the Identification Changes dialog box shown in Figure 4-8.
Figure 4-8. The Identification Changes dialog
WARNING
After you press the OK button, Windows should present you with a small dialog box welcoming you to the domain. When you click the OK button in this dialog box, you will be told that you need to reboot the computer. Click the OK button in the System Properties dialog box, and reboot the computer as requested. When the system comes up again, the machine will automatically present you with a Log On to Windows dialog box similar to the one shown in Figure 4-9.
Figure 4-9. The Windows 2000 logon window
WARNING
Enter the username and password of any Samba-enabled user in the User name: and Password: fields, and either press the Enter key or click the OK button. If it worked, your Windows session will start up with no error dialogs.
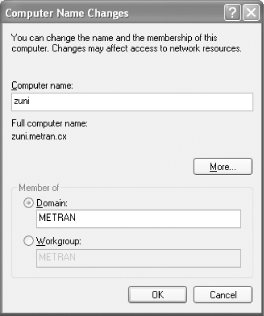
Windows XP Professional
To configure Windows XP Professional for domain logons, log in to the computer as Administrator or another user in the Administrators group, open the Control Panel in Classic View, and double-click the System icon to open the System Properties dialog box. Click the Computer Name tab and then click the Change... button. You should now see the Computer Name Changes dialog box shown in Figure 4-10.
Figure 4-10. The Computer Name Changes dialog
WARNING
After you press the OK button, Windows should present you with a small dialog box welcoming you to the domain. When you click the OK button in this dialog box, you will be told that you need to reboot the computer to put the changes into effect. Click the OK buttons in the dialog boxes to close them, and reboot the computer as requested. When the system comes up again, the machine will automatically present you with a Log On to Windows dialog box similar to the one shown in Figure 4-11.
Figure 4-11. The Windows XP logon window
WARNING
Enter the username and password of any Samba-enabled user in the User name: and Password: fields, and either press the Enter key or click the OK button. If it worked, your Windows session will start up with no error dialogs.
Logon Scripts
In a Unix environment, the ability to run such a script might lead to a very complex initialization and deep customization. However, the Windows environment is mainly oriented to the GUI, and the command-line functions are more limited. Most commonly, the logon script is used to run a net command, such as net use, to connect a network drive letter, like this:
net use T: \\toltec\test
This command will make our [test] share (from
Chapter 2) show up as the T: drive in My Computer.
This will happen automatically, and T: will be available to the user
at the beginning of her session, instead of requiring her to run the
net use command or connect the T: drive using
the Map Network Drive function of Windows Explorer.
Another useful command is:
net use H: /home
which connects the
user's home directory to a drive letter (which can
be H:, as shown here, or some other letter, as defined by
logon drive). For this to work,
you must have a [homes] share defined in your
smb.conf file.
If you are using roaming profiles, you should definitely have:
net time \\toltec /set /yes
Creating a Logon Script
In our smb.conf file, we have the line:
logon script = logon.bat
This defines the location and name of the logon script batch file on
the Samba server. The path is relative to the
[netlogon] share, defined later in the
file like this:
[netlogon] path = /usr/local/samba/lib/netlogon writable = no browsable = no
Notice also that the extension of our logon script is .bat. Be careful about this—an extension of .cmd will work for Windows NT/2000/XP clients, but will result in errors for Windows 95/98/Me clients, which do not recognize .cmd as an extension for batch files.
Because the logon script will be executed on a Windows system, it must be in MS-DOS text-file format, with the end of line composed of a carriage return followed by a linefeed. The Unix convention is a newline, which is simply a linefeed character, so if you use a Unix text editor to create your logon script, you must somehow make it use the appropriate characters. With vim (a clone of the vi editor that is distributed with Red Hat Linux), the method is to create a new file and use the command:
:se ff=dos
to set the file format to MS-DOS style before typing in any text. With emacs, the same can be done using the command:
^X Enter f dos Enter
where ^X is a Control-X character and
Enter is a press of the Enter key. Another method
is to create a Unix-format file in any text editor and then convert
it to MS-DOS format using the
unix2dos program:
$unix2dos unix_file >logon.bat
#!/usr/bin/perl open FILE, $ARGV[0]; while (<FILE>) { s/$/\r/; print }
Or, you can use Notepad on a Windows system to write your script and then drag the logon script over to a folder on the Samba server. In any case, you can check the format of your script using the od command, like this:
$od -c logon.bat
You should see output resembling this:
0000000 n e t u s e T : \ \ t o l 0000020 t e c \ t e s t \r \n 0000032
One method is to use variables inside the logon script that cause commands to be conditionally executed. For details on how to do this, you can consult a reference on batch-file programming for MS-DOS and Windows NT command language. One such reference is Windows NT System Administration, published by O'Reilly.
Windows batch-command language is very limited in functionality.
Fortunately, Samba also supports a means by which customization can
be handled. The
smb.conf file contains variables that can be
used to insert (at runtime) the name of the server
(%L), the username of the person who is
accessing the server's resources
(%u), or the computer name of the client
system (%m). To give an example, if we set up the
path to the logon script as:
logon script = %u/logon.bat
we would then put a directory for each user in the
[netlogon] share, with each directory named the
same as the user's username, and in each directory
we would put a customized logon.bat file. Then
each user would have his own custom logon script. We will give you a
better example of how to do this kind of thing in the next section,
Section 4.5.
TIP
For more information on Samba configuration file variables, such as the
%L,%u, and%mvariables we just used, see Chapter 6 and Appendix B.
When modifying and testing your logon script, don't
just log off of your Windows session and log back on to make your
script run. Instead, restart (reboot) your system before logging back
on. Because Windows often keeps the [netlogon]
share open across logon sessions, the reboot ensures that Windows and
Samba have completely released and reconnected the
[netlogon] share, and the new version of the logon
script is being run while logging on.
More information regarding logon scripts can be found in the O'Reilly book, Managing Windows NT Logons.
Roaming Profiles
One benefit of the centralized authentication of Windows NT domains is that a user can log on from more than just one computer. To help users feel more "at home" when logged on at a computer other than their usual one, Microsoft has added the ability for users' personal settings to "roam" from one computer to another.
When the profile is stored on the local system, it is called a local profile. On Windows NT, local profiles are stored in C:\winnt\profiles. On Windows 2000/XP, they can be found in C:\Documents and Settings. On Windows 95/98/Me, when configured for a single user (the default case), the local profile is scattered in places such as the registry and directories such as C:\Windows\Desktop and C:\Windows\Start Menu. When Windows 95/98/Me is configured for multiple users, the local profile of the preexisting user is moved to a folder in C:\Windows\Profiles that has the same name as the user, and any users that are subsequently added to the computer have their local profiles created in that directory as well. You can browse through the local profiles to see their structure—each has a